FGRE 2015: Tutorial
In this page you can find instructions in order to attend the SmartFIRE tutorial on NITOS testbed, given at Fed4FIRE GENI Research and Experiment Summit 2015.
If you encounter any problems while running the tutorial, you can contact Donatos Stavropoulos (This email address is being protected from spambots. You need JavaScript enabled to view it. ).
The topology of the experiment consists of 6 nodes and is illustrated in the figure below.
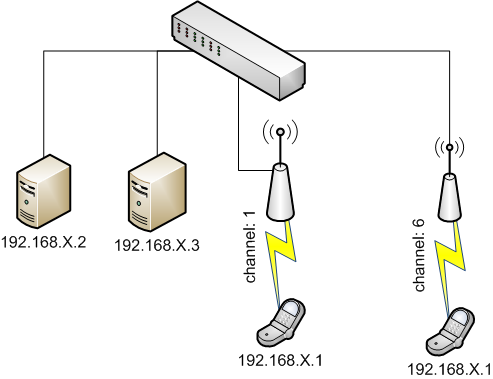
In particular, 2 senders, 2 receivers and 2 bridges. The senders and the bridges are connected through their wired interface (eth1) with a L2 Ethernet switch, while the two bridges are connected with the two receivers using their wireless interfaces (wlan0) and different wireless channels.
The receivers use the same IP address (192.168.X.1) and each of the two senders (192.168.X.2 & 192.168.X.3 where X equals your FGRE slice number fgre1-fgre6) trys to send 1Mbps traffic to one of the two receivers. In particular, the senders initiate an ARP request for mapping the IP address 192.168.X.1 to the MAC address of one of the two receivers. Since the two receivers reply with their own ARP reply, once they receive the ARP request, the bridges behave as OpenFlow switches that filter these replies and forward only one of them, based on the ARP requester. Configuring the openflow controller, the experimenter is able to control the receiver of each sender.
The steps that you have to follow in order to experiment with wireless and SDN resources are the following:
- Connect to NITOS server through ssh, using one of the available slices fgre* (fgre1 - fgre6). The password will be given during the tutorial.
fgre1-fgre2:
ssh fgre*@nitlab.inf.uth.gr
fgre3-fgre6:
ssh fgre*@nitlab3.inf.uth.gr - Run the OMF experiment using the experiment description fgre.rb, that is available at the home folder of your slice. During the execution, information will be provided through the console output, including the OMF Experiment ID - omf_exp_id. The results of this experimentation are stored through the OML framework to a database, and will be visualized later.
omf exec fgre.rb --slice fgre*
- Visualize the results by connecting to the OMF web server in another console, using the same username as before (the name of the slice).
ssh fgre*@83.212.32.166
- Run the OMF web server, executing the script that is named fgre.sh and is located in the omf_web_nitos_fgre_2015 folder (The OMF Experiment ID - omf_exp_id is provided through the information given in the OMF experiment execution).
cd omf_web_nitos_fgre_2015
./fgre.sh omf_exp_id - View the experimentation results at the following URL, using the appropriate port depending on your slice (fgre* -> 310*, e.g. fgre1 -> 3101).
http://83.212.32.166:310*
Who's Online
We have 14 guests and no members online


